Golden Dome: Nonkinetic weapon performance methods for negating and automating asymmetric missile-defense threats left of launch
StoryOctober 10, 2025

Current global instability, continued proliferation of medium- and long-range missiles, and increasingly sophisticated threats such as maneuvering reentry vehicles pose significant challenges for fielded ballistic missile defense systems (BMDSs). In response to progressively heightened real-time threats, Golden Dome’s three-year gauntlet has been laid down. Exponential technology evolution has created broad-spectrum, nonkinetic opportunities to qualitatively augment BMDS. A probabilistic “system of systems” (SoS) approach is described to harness kinetic, nonkinetic, and automated cross-domain access and transfer solutions for enabling secure C5ISR [command, control, computers, communications, cyber, intelligence, surveillance, and reconnaissance] systems and artificial intelligence (AI) platform interoperability. The cross-domain solutions can then be expeditiously deployed from cloud service provider (CSP) data centers to the tactical edge. The SoS approach aids enhanced qualitative decision-making and effector competence to satisfy complex battle operations “left of launch.”
Well-known solutions exist that provide performance assessment of kinetic solutions. Probability of single shot engagement kill (PSSEK) measures effectiveness but considers only kinetic means to neutralize a ballistic missile threat. PSSEK expresses the reliability of the combat system operating correctly as Pes and Pcs, and the probability of the interceptor neutralizing the threat (PSSK).
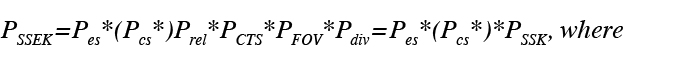
 Probabilities:
Probabilities:
- Pes: system engagement support services operate correctly,
- Pcs: operational reliability of system communication,
- Prel: interceptor, kill vehicle, and missile reliability,
- Pcts: correct target selection,
- Pcontain: interceptor can contain a threat given the engagement support =PFOV*Pdiv where PFOV is the probability user has field-of-view containment and,
- Pdiv: diverting containment.
These methods for calculating success are notional at best and ambiguous in often vast, complex environments, necessitating new solutions.
Moreover, the Common Vulnerability Scoring System (CVSS) exists to identify and prioritize vulnerabilities that pose the greatest risk. However, vulnerabilities are assigned arbitrary scores, and CVSS does not provide a method to convert scores into probability distributions.
An SoS approach is proposed for providing a comprehensive and task-oriented environment specifically focused on the needs of current BMDS rather than less beneficial enhancements to combat systems, sensor performance or interceptors. An SoS approach supports more informed decision-making and improved overall missile defense.
Traditional kinetic-only missile-defense methods need to evolve to a more holistic and contextually achievable asymmetric missile defense (AMD) approach (Figure 1).
.jpg)
[Figure 1 ǀ A diagram shows a layered asymmetric missile defense (AMD) operational view.]
Integrated kinetic and nonkinetic battle management
The AMD is a four-layer approach providing a mathematical method and algorithms to automatically combine and assess the performance of nonkinetic and kinetic techniques for negating missile threats. AMD integrates cyber technologies; intelligence, surveillance, and reconnaissance (ISR) knowledge; processing exploitation and dissemination (PED); analytics; artificial intelligence (AI); and electronic warfare (EW). These includes proven techniques like decoys and battle management (kinetic and nonkinetic) for negating missile threats, not only during flight phases but more importantly “left of launch,” the term used to describe the strategy of taking preemptive actions to prevent an attack or threat before it happens.
Figure 1 illustrates a layered AMD operational view depicting integrated kinetic and nonkinetic battle management of detectable vulnerabilities. The graphic depicts sensing types and their notional ranges for supporting enhanced effector actions. The red outline shows a potential interdiction option, months in advance of launch, which could disrupt an adversary’s use of required raw materials.
AMD’s four layers are:
- The core level, where a Pnegation (Pn) score is computed for each Vulnerability and Technique (VT) pair.
- A temporal level that converts VT scores into random variables, derives probability distribution functions for each and establishes conditions Pn(VT) for Time (Ti), where Pn(VTTi) is calculated for each VT pair.
- The Battle Damage Assessment (BDA) level, where Pn(VTTi) values relate the potential technique used with probability of deployment validation (Pvd) or (Ptip) and probability of mitigation verification (Pv,n).
- A terminal phase level Pn, calculated by combining Pn values related to each of the AMD layers.
Figure 2 depicts BMDS threat vulnerability focus points by phase, where computations are based upon platform, sensor type, and availability of required intelligence to optimize the probability of negation Pn. Simple and complex negation opportunities and scenarios drive required responses.
.jpg)
[Figure 2 A diagram shows BMDS threat vulnerability focus points by phase.]
Responses to all questions drive probability Ptip values, where:
- POCCURRENCE: enemy indication of imminent action will occur,
- PAVAILABLE: friendly ISR assets are available when enemy indication occurs,
- PSENSE: friendly ISR assets may be able to detect enemy indication,
- PTIME: tip from friendly ISR is timely enough to enable blue force (BF) tactical response,
- Ptip: successful tip from friendly ISR assets.

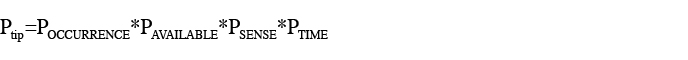
Automating embedded and enterprise analysis and negation
Complex multidomain, multimodality, real-time threat regions must consider many distributed platforms, AI deployments, sensors, effectors, and decision-makers. These complexities necessitate more rapid interoperability and autonomy to enable real-time response and effective negation. Simultaneously, an instantaneous adversarial response requires deployment of more adaptive capabilities and rapid injection of new capabilities, including eventual autonomous DevSecOps [development, security, and operations].
Each of these systems operates on networks at varying classification levels. Every physical device, sensor, platform AI analysis system, and user must be able to access these networks from varying threat-level access points. Mitigating these challenges and increasing effective autonomy for real-time threat negation requires accredited high-speed enterprise and embedded cross-domain solutions (CDSs).
CDSs provide data integrity to enable secure, automated, multi-classification operations. This provides enforced unidirectional flow, malware removal, and highly enforced data integrity. Finally, proper placement, automated configurations, and system-integrity functions provide scalable CDS, which can then be expeditiously deployed from cloud service provider (CSP) data centers to the tactical edge.
BDMS going forward
To mitigate increasingly sophisticated threats and challenges for fielded BMDS, a probabilistic four-layer AMD SoS approach can be used. This approach responds to multidomain, real-time threats, automated integration of AI technologies, and a broad spectrum of nonkinetic techniques to create substantial asymmetric opportunities to qualitatively augment BMDS. This SoS approach can harness kinetic and no-kinetic opportunities to detect adversary vulnerabilities and automate C5ISR with cross-domain system interoperability. Leveraging and extending existing effective solutions can mitigate real-time threats, even those “left of launch.”
Dr. John Carbone is Senior Technical Director and Chief Solutions Architect at Everfox. He is also an eight-year Adjunct Professor of Applied AI and Data Science at Baylor University. Dr. Carbone has more than 37 years of experience engineering U.S. defense-industry mission-critical warfighting systems across C5ISR systems, high-performance computing, cloud, modeling, and kill-chain optimization from operations centers to the tactical edge. He holds GIS, data-science, and missile-defense patents, and has published more than 100 AI, engineering, and data science books/publications. Readers may reach Dr. Carbone at [email protected].
Everfox https://www.everfox.com/
References
1. Hershey, Paul C., Robert E. Dehnert, John J. Williams, John N. Carbone, Jeanne M. Robinson, and David J. Wisniewski. “Method for non-kinetic performance assessment.” U.S. Patent 9,779,191 issued October 3, 2017.
2. Brown, G., et al. “A two-sided optimization for theater ballistic missile defense.” Operations research 53.5 (2005): 745-763.*
3. Mell, P., et al. “Common vulnerability scoring system.” Security & Privacy, IEEE 4.6 (2006): 85-89.*
4. Garrett, R., et al. “Managing the interstitials, a system of systems framework suited for the ballistic missile defense system.” Systems
5. Pate-Cornell, E. “Fusion of intelligence information: A Bayesian approach.” Risk Analysis 22.3 (2002): 445-454.*
6. Kopp, Carlo, et al., “High Energy Laser Directed Energy Weapons”, © 2006-2012 Carlo Kopp, Technical Report APA-TR-2008-0501, Defense Today, 2006 Series, (May 2008), 39 pgs.
7. Mell. Peter, et al., “CVSS, A Complete Guide to the Common Vulnerability Scoring System”, Version 2.0 National Institute of Standards and Technology, Carnegie Mellon University, (Jun. 2007), 1-23.
8. Shein, Rob, “A Brief Summary of Cyber Warfare”, Information Security Management Handbook, Sixth Edition, vol. 4, Tipton, H.F., et al., Editors, Auerbach Publications, (2010), 6 pgs.




