Military Embedded Systems
Op-Eds
Comms
CSfC Technology Day 2019 recap - Blog
October 31, 2019Unmanned
Hypersonic vehicles and the kill web - Blog
September 30, 2019Radar/EW
Radar and the kill web - Blog
July 31, 2019Comms
How Ethernet is key to VICTORY - Blog
June 28, 2019Radar/EW
Enemy ships and the kill web - Blog
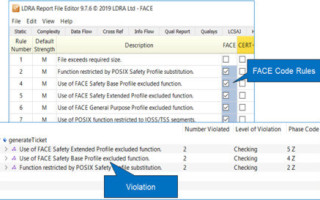
June 27, 2019FACE approach improves affordability, time-to-field of avionics systems and software platforms - Blog
June 19, 2019A.I.
Radar/EW
Strategic intelligence and the kill web - Blog
May 31, 2019Vendor backing grows for the emerging FACE standard - Blog
April 30, 2019Radar/EW
Problems with the kill web: Moving from C4ISR to SNAI - Blog
March 27, 2019Radar/EW
Keep pace with a standardized development process - Blog
February 28, 2019Cyber
Integrity of embedded systems - Blog
February 28, 2019It is critical to be able to verify the integrity of systems used in military and other applications to ensure that they have not been modified or corrupted. It is of course best to prevent a system from being tampered with. If this can't be done, it is vital to detect tampering. In many cases it is better to prevent a system from operating at all if you can't be sure it hasn't been modified. In all cases it is vital to protect information on the system and especially critical secrets like crypto keys.
Cyber
Comms
Fiber and copper working together for today's Ethernet backbones - Blog
January 31, 2019-
Holt Releases First ARINC 429 Quad Line Driver
January 28, 2026
-
Top 10 Military Embedded Systems stories of 2025
January 19, 2026
-
E-2D identification friend or foe service depot to be established for U.S. Navy by BAE Systems
January 15, 2026
-
GUEST BLOG: From code to behavior – Software assurance in safety- and mission-critical edge systems
January 15, 2026
-
Missile production expansion agreements signed by Raytheon, DoD
February 04, 2026
-
Counter-drone batteries to be provided to Poland by Kongsberg and PGZ
February 02, 2026
-
Advanced sensing and targeting system for ship defense to be developed for DARPA by Raytheon
February 02, 2026
-
V-BAT drones and Hivemind software to be supplied to Indian Army by Shield AI
January 30, 2026
-
TRML-4D air defense radars to be provided to European users by HENSOLDT
February 03, 2026
-
Infrared search-and-track sensors to be provided to Taiwan by Lockheed Martin
February 03, 2026
-
Sonobuoy pact signed between U.K. MoD and Ultra Maritime
February 02, 2026
-
Electronic warfare integration and sustainment for U.S. Army to be performed by CACI
January 28, 2026
-
Artificial intelligence platform provider AIM wins $4.9 million Air Force contract
January 22, 2026
-
SOSA aligned SBC with advanced AI capabilities introduced by Abaco Systems
January 15, 2026
-
AI-driven training environment for Space Force garners $27 million contract
January 15, 2026
-
AI/ML contract for embedded operations signed by SRC, AFRL
January 14, 2026